

The Anatomy of a Cyber Incident
Table of Contents
Understanding Cyber Incidents: Why Every Business Needs to Know What They Are
A cyber incident is an event that actually or potentially jeopardizes the confidentiality, integrity, or availability of your information or systems. It’s a confirmed threat that requires immediate action, unlike a minor cyber event (like a failed login), which may only need monitoring.
Quick Answer: What is a Cyber Incident?
- Definition: Any occurrence that harms or may harm your organization’s data, systems, or operations.
- Key Impact Areas: Confidentiality (unauthorized access), Integrity (unauthorized changes), and Availability (system disruption).
- Common Examples: Data breaches, ransomware, phishing scams, denial-of-service attacks.
- Critical Fact: The average cyber incident costs a business $4.35 million and can go undetected for months.
Understanding this distinction is crucial. Incidents demand a full-scale response, including containment, investigation, and recovery. Events, while important to track, don’t always trigger this emergency protocol.
These threats aren’t abstract statistics; they represent real businesses facing operational disruption, financial loss, and damaged customer trust. The frequency and sophistication of cyberattacks are constantly increasing, making proactive defense a necessity for survival.
I’m Randy Bryan, founder of tekRESCUE. I’ve helped countless Central Texas businesses steer the aftermath of cyber incidents and build stronger defenses. In this guide, I’ll share practical insights to help you protect your business, from understanding official definitions to implementing effective response strategies.

Navigating a Cyber Incident: Reporting, Response, and Roles

When a cyber incident hits, your response in the first few hours is critical. A clear plan and knowing who to call can prevent a manageable disruption from becoming a catastrophe. For businesses in Central Texas and the DFW area, this roadmap helps you steer the chaos.
Defining and Preparing for a Cyber Incident
Preparation is your best defense. According to NIST’s official definition of a cyber incident, it’s any event that threatens your digital assets. Being prepared means having these key elements in place:
- Incident Response Plan (IRP): Your documented roadmap outlining roles, communication channels, and technical steps for containment, eradication, and recovery.
- Tabletop Exercises: Simulated incident scenarios that pressure-test your IRP and train your team to respond instinctively, revealing gaps before a real attack does.
- Network Segmentation: Dividing your network into isolated segments to contain breaches and limit an attacker’s movement, much like fire doors in a building.
- Data Backups: Regular, secure, and offline backups are your non-negotiable safety net, allowing you to restore data after a ransomware attack without paying a ransom.
- Communication Strategy: A plan that includes out-of-band communication channels (like personal phones) and pre-approved templates for notifying stakeholders, including employees, customers, and regulators.
The Critical Role of Reporting: Legal and Regulatory Mandates
Ignoring a cyber incident can be illegal. A growing number of regulations mandate timely reporting, and failure to comply leads to severe fines and legal action.
- CIRCIA: The Cyber Incident Reporting for Critical Infrastructure Act will require covered entities to report incidents to CISA within 72 hours and ransom payments within 24 hours.
- NCUA Part 748: Federally insured credit unions must report a reportable cyber incident no later than 72 hours after discovery.
- SEC Rules: Publicly traded companies must disclose material cyber incidents and their cybersecurity governance.
- HIPAA: Healthcare entities must notify affected individuals and HHS of any breach of protected health information.
| Feature | CIRCIA (Proposed) | NCUA Part 748 (Effective) |
|---|---|---|
| Timeline for Incident | 72 hours after reasonable belief of covered cyber incident | As soon as possible, no later than 72 hours after reasonable belief |
| Timeline for Ransom | 24 hours after making a ransom payment | Falls under general incident reporting if critical |
| Who Reports | Covered entities in critical infrastructure sectors | Federally Insured Credit Unions (FICUs) |
| What to Report | Covered cyber incidents, ransom payments | Reportable cyber incidents (impacted services, data compromise, operational impact) |
The consistent theme is urgency. These tight deadlines underscore why a practiced IRP is essential. Non-compliance adds regulatory penalties and legal fees to the already high cost of a data breach.
Who Responds? Government Agencies and Private Sector Experts
You don’t have to face a cyber incident alone. A network of public and private entities is available to help.
Government agencies like CISA (the nation’s cyber defense agency), the FBI (which investigates cybercrime), and the Secret Service (which combats financial fraud) provide critical support. CISA encourages voluntary reporting at CISA’s voluntary reporting guidance to help protect the broader business community. These agencies focus on threat attribution, asset protection, and bringing criminals to justice.
Private sector experts, like incident response firms, provide hands-on technical assistance. These teams specialize in digital forensics to understand the breach, containment to stop the spread, and recovery to restore operations. At tekRESCUE, our incident response services provide businesses in Central Texas with the specialized expertise needed to manage an attack from start to finish. We help build your IRP, run tabletop exercises, and provide rapid response when you need it most.
The Evolving Threat Landscape and Building Resilience

The digital threat landscape is constantly changing, with new attack methods and more sophisticated criminals emerging daily. Understanding these trends helps businesses in Texas and beyond build stronger, more resilient defenses.
Lessons from Real-World and International Incidents
Recent major cyber incidents offer critical lessons for every business. A faulty software update in 2024 from a single vendor caused worldwide disruptions, highlighting the immense danger of third-party risk. Your security is only as strong as the weakest link in your supply chain.
Ransomware remains a devastating threat. Attacks like the one on Tarrant County, which exposed taxpayer data, prove that these are not distant problems but local realities affecting our communities. This underscores why offline, air-gapped backups are non-negotiable; they can be the only thing standing between a quick recovery and a catastrophic loss.
Furthermore, state-sponsored cyber espionage has escalated, targeting not just governments but also private businesses to steal intellectual property and disrupt operations. These well-funded groups are patient and persistent, making robust security a matter of competitive survival.
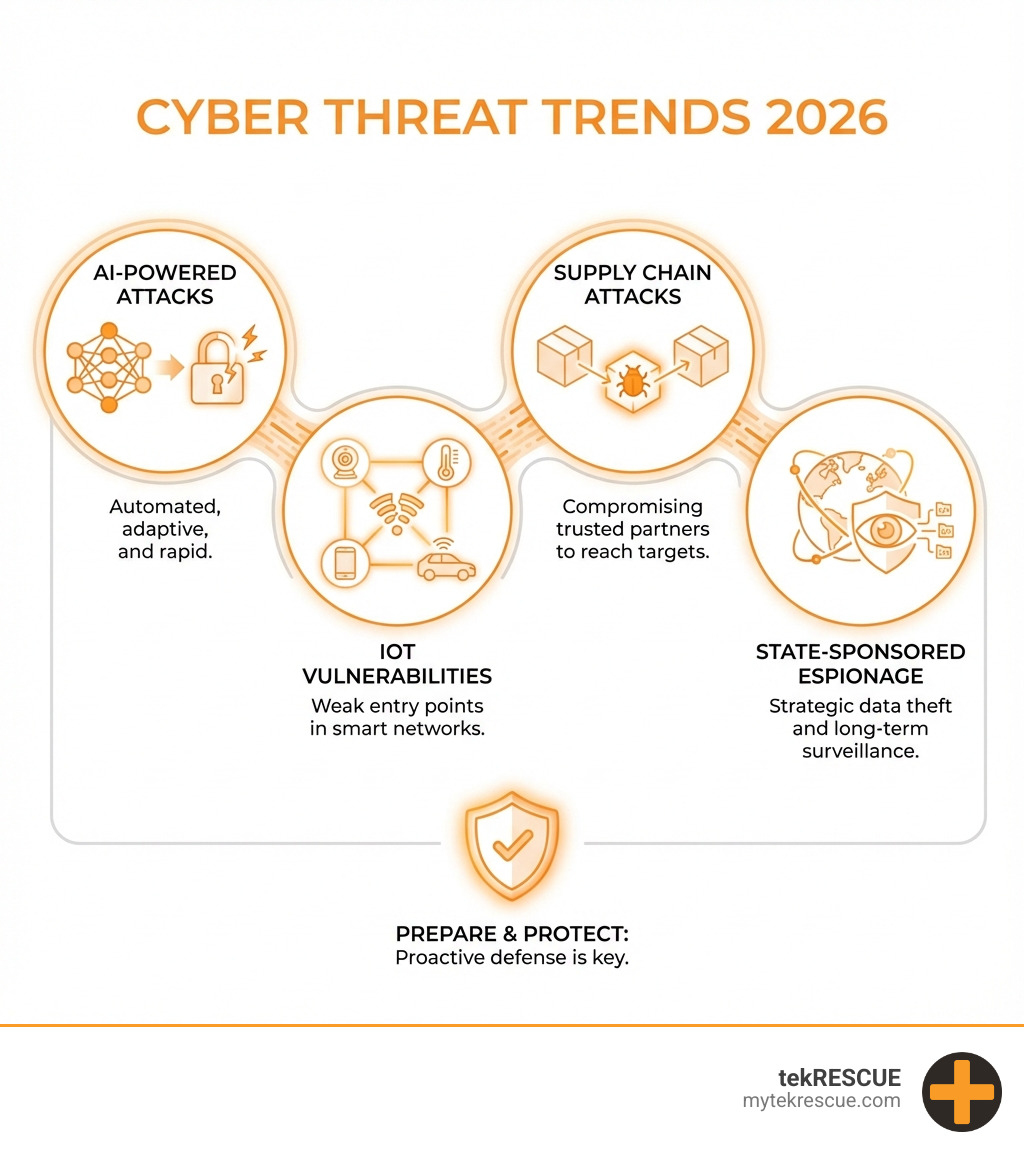
Emerging Threats and Key Resources for Your Business
Staying informed is crucial to managing risk. Key emerging threats include:
- AI-Powered Attacks: Criminals use AI to create highly convincing phishing emails and automate attacks, making them harder to detect.
- IoT Vulnerabilities: Every smart device on your network, from cameras to thermostats, is a potential entry point for attackers.
- Supply Chain Compromises: Attackers increasingly target software suppliers to gain access to thousands of their customers at once.
Fortunately, you don’t have to face these threats alone. Excellent resources are available to help you build a strong security posture:
- The NIST Cybersecurity Framework provides a gold-standard model for managing cybersecurity risk.
- StopRansomware.gov offers free, actionable guidance from federal agencies on preventing and responding to ransomware.
- Information Sharing and Analysis Centers (ISACs) provide industry-specific threat intelligence to give you early warnings.
At tekRESCUE, our incident response services help businesses in San Marcos TX, Central Texas, and the DFW area prepare for these evolving threats. Proactive investment in cybersecurity is far less costly than the average $4.35 million price tag of a data breach.
Conclusion: Creating a Proactive Defense Against the Next Cyber Incident
The landscape of cyber incidents is complex and costly, with the average breach costing millions. Waiting for an attack is a risk no business can afford. The key to survival is shifting from a reactive to a proactive security posture.
This means building resilience through practical steps: develop and practice an incident response plan, segment your network, maintain secure offline backups, and understand your legal reporting obligations. As we’ve discussed, no solution is 100% foolproof, but these measures substantially reduce your risk and prepare you to respond effectively when an incident occurs.
Protecting your data, reputation, and future is paramount. You don’t have to do it alone. At tekRESCUE, we help businesses across Central Texas build the proactive defenses they need to thrive in a challenging digital world.
For expert guidance on developing a robust incident response plan and strengthening your cybersecurity, contact tekRESCUE at (512) 843-2835 or visit our website. We serve businesses in San Marcos TX, Central Texas, and the DFW area.
Schedule a comprehensive cybersecurity audit today.
TL;DR / Quick Summary
Here’s a rapid summary of what every business owner needs to know about a cyber incident.
-
What it is: A confirmed threat to your data or systems that requires immediate action. It’s a business-critical event, not just an IT problem, with an average cost of $4.35 million per breach.
-
Reporting is often mandatory: Laws like CIRCIA, NCUA Part 748, and HIPAA require reporting incidents within tight deadlines (often 72 hours). Failure to comply results in heavy fines.
-
You are not alone: Government agencies (CISA, FBI) and private firms like tekRESCUE provide critical support for investigation, containment, and recovery.
-
Threats are evolving: AI-powered attacks, supply chain compromises, and IoT vulnerabilities are on the rise. Proactive defense is essential.
-
The bottom line: Proactive preparation through planning, backups, and expert guidance is the most effective way to reduce the risk and impact of a cyber incident.
Ready to strengthen your defenses? tekRESCUE offers incident response planning and security services for businesses in San Marcos TX, Central Texas, and the DFW area. Learn more about our incident response services or call us at (512) 843-2835.
FAQ
What is a cyber incident?
A cyber incident is a confirmed security event that threatens the confidentiality, integrity, or availability of your data or systems. Unlike a minor event (like a failed login), an incident is a verified compromise—such as a ransomware attack or data breach—that requires immediate response and containment.
How do I report a cyber incident?
Reporting depends on your industry. Federally insured credit unions report to the NCUA within 72 hours. Critical infrastructure entities will soon report to CISA under CIRCIA. For criminal matters, contact your local FBI field office or report through IC3.gov. You can also voluntarily report to CISA at report@cisa.gov to help protect other businesses.
What are the legal requirements for reporting?
Legal requirements vary by sector but often mandate quick action. CIRCIA proposes a 72-hour reporting window for incidents and 24 hours for ransom payments. NCUA Part 748 requires reporting within 72 hours. SEC rules require public companies to disclose material incidents, and HIPAA mandates breach notification for healthcare data. Missing these deadlines can lead to significant fines and legal penalties.
Who should be involved in incident response?
Effective incident response requires a team. Internally, this includes IT, legal, communications, and management. Externally, you should involve a private incident response firm like tekRESCUE for specialized technical expertise. Government agencies like CISA and the FBI are also key partners for coordination and investigation.
How can my business reduce cyber risk?
Reducing risk starts with proactive preparation. Key steps include creating and practicing an Incident Response Plan (IRP), maintaining secure offline backups, segmenting your network to limit damage, and training employees on security awareness. Partnering with a cybersecurity expert to assess vulnerabilities and manage threats is a smart investment, as proactive measures cost a fraction of the average $4.35 million data breach.
Table of Contents









