

Fortify Your Defenses: Steps to Prevent Ransomware Attacks
How to prevent ransomware starts with understanding the threat and implementing multiple layers of defense. Here are the essential steps every business must take:
Immediate Prevention Steps:
- Keep software updated – Install security patches for operating systems and applications
- Use endpoint security – Deploy antivirus and anti-malware solutions
- Enable Multi-Factor Authentication – Add extra security layers to user accounts
- Create offline backups – Follow the 3-2-1 backup rule with immutable storage
- Train employees – Teach staff to identify phishing emails and suspicious links
- Segment networks – Isolate critical systems to limit ransomware spread
- Prepare incident response – Have a plan ready before an attack occurs
Ransomware is malicious software that encrypts your business data and demands payment for its release. These attacks have become the second-most common cybersecurity incident, appearing in almost 16% of all security breaches.
The financial impact is staggering. The WannaCry attack in 2017 infected an estimated 200,000 computers worldwide and caused $4 billion in total damages. FortiGuard Labs reports an average of 150,000 ransomware detections each week, showing this threat continues to grow.
Small and medium businesses are prime targets because attackers assume they have weaker security systems and less cybersecurity expertise. Yet the consequences can be devastating – from operational shutdowns to permanent data loss to reputation damage.
The good news? Most ransomware attacks are preventable with the right combination of technology, processes, and training.
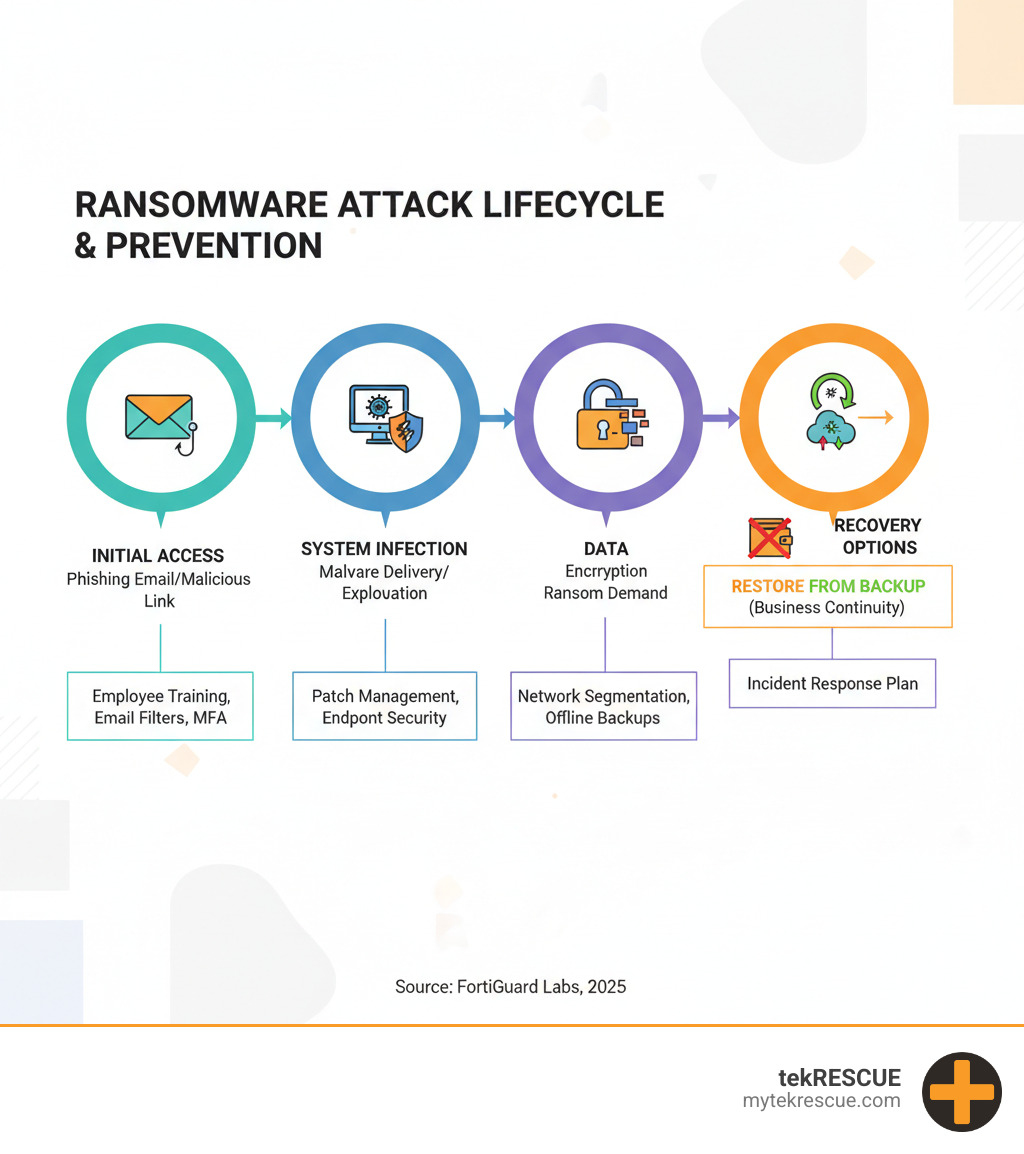
Table of Contents
A Layered Defense: Your Step-by-Step Guide on How to Prevent Ransomware
Think of ransomware protection like securing your home. You wouldn’t rely on just a front door lock—you’d want security cameras, motion lights, and maybe even a security system. The same principle applies to preventing ransomware: we need multiple layers of defense working together.
This approach is called “defense in depth,” and it’s your best strategy against ransomware attacks. When cybercriminals try to breach one security layer, another layer stops them in their tracks. Even if they manage to slip past your first line of defense, they’ll hit a wall somewhere else in your security stack.
Here’s the reality: ransomware typically sneaks into your system through vulnerabilities, then encrypts your files and demands payment (usually in cryptocurrency like Bitcoin) to unlock them. But paying doesn’t guarantee you’ll get your data back—and it often makes you a bigger target for future attacks. That’s why prevention beats recovery every single time.
Fortify Your Technical Infrastructure to Help Prevent Ransomware
Your technical infrastructure is like the foundation of your digital security house. Without a solid foundation, everything else becomes shaky. Let’s start with the basics that make the biggest difference.
Software updates and security patches are your first and most critical defense. Remember the devastating WannaCry attack? It spread like wildfire through systems that hadn’t installed available Windows security patches. Cybercriminals actively hunt for known vulnerabilities in outdated software, so keeping everything current closes these security gaps before attackers can exploit them.
Endpoint security acts as your digital bodyguard on every device connected to your network. Modern antivirus and anti-malware solutions do much more than scan for known threats—they watch for suspicious behavior that might indicate a ransomware attack in progress.

Look for endpoint protection that includes real-time threat detection to continuously monitor for suspicious activity, behavioral analysis that identifies ransomware by its actions rather than just known signatures, exploit prevention to block attempts to take advantage of software vulnerabilities, and rollback capabilities that can actually reverse changes made by ransomware.
Network segmentation is like having fire doors in a building—it contains threats and prevents them from spreading. Instead of having one big, open network where ransomware can move freely between systems, you create separate network segments. If ransomware infects one segment, it can’t easily jump to your critical business systems in another segment.
Finally, firewalls and Intrusion Detection and Prevention Systems (IDPS) serve as your network’s security guards. Firewalls control what traffic can enter and leave your network, while IDPS actively monitors for malicious activity and can automatically block threats. When properly configured, these systems dramatically reduce your attack surface.
How to Prevent Ransomware with a Zero Trust Security Framework
The old “trust but verify” approach to network security just doesn’t cut it anymore. Today’s threat landscape demands a Zero Trust model that operates on “never trust, always verify.” This assumes that threats can come from anywhere, both outside and inside your network, so every access request must be authenticated and authorized.
The principle of least privilege is the cornerstone of Zero Trust. Simply put, give users and systems only the minimum access they need to do their jobs, nothing more. Your marketing team doesn’t need access to your financial servers, and your accounting staff doesn’t need administrative rights to your entire network. It’s like giving employees only the keys they need for their specific work areas, not the master key to everything.
Multi-Factor Authentication (MFA) adds crucial extra layers beyond just passwords. Even if cybercriminals steal a password. They still need that second factor, like a code from a phone app or a biometric scan, to gain access. This simple step stops the vast majority of unauthorized access attempts.
User access controls and network access restrictions ensure that every connection to your systems is properly verified. This is especially important for remote workers and administrative accounts, which are prime targets for ransomware attackers. Administrative privileges should be limited to essential personnel only, with strict security measures including strong MFA and session monitoring.
For a complete roadmap on implementing this powerful security approach, our Zero Trust Security Implementation Guide for Small and Medium Businesses walks you through each step.
Create an Immutable Data Backup and Recovery Plan
If ransomware is like a fire threatening your business, then data backups are your fire insurance, escape route, and rebuilding plan all rolled into one. This might be the single most important step in how to prevent ransomware from destroying your business. When you can restore your data quickly and completely, ransomware loses its power over you.
The 3-2-1 backup rule is your foundation: keep three copies of your data (your original plus two backups), store them on two different types of media (like local servers and cloud storage), and keep one copy offsite in a geographically separate location.
But here’s the crucial part: some of your backups must be offline backups or stored in immutable storage. Offline backups are physically disconnected from your network, so ransomware can’t reach them to encrypt them. Immutable storage means once the data is written, it cannot be altered or deleted—even by ransomware that might lurk in your systems for weeks before striking.
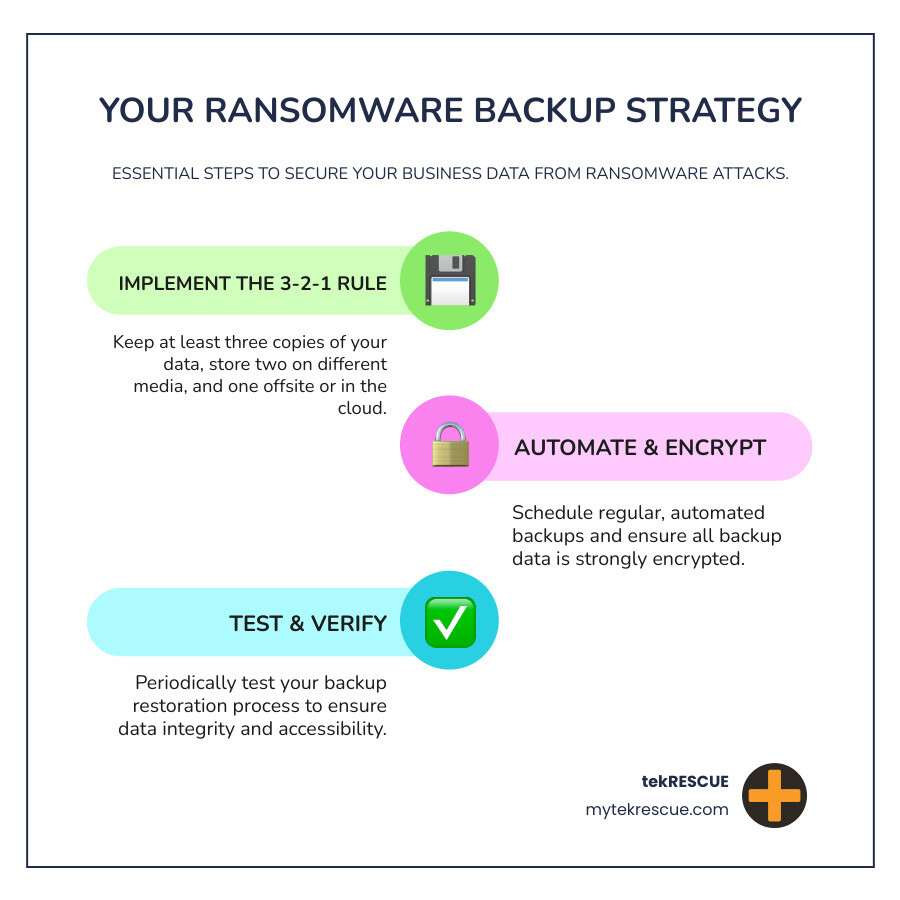
Cloud storage offers excellent backup options with built-in ransomware detection, recovery features, and file versioning. This lets you roll back to clean versions of your files if an attack occurs. However, having backups isn’t enough—you need a solid recovery plan and must test your backups regularly.
Think of backup testing like fire drills. You wouldn’t wait for an actual fire to see if your escape plan works. Regular testing ensures your backups are intact, uncorrupted, and that you can restore your systems quickly when every minute counts. If the worst does happen, our Data Breach Response Checklist provides the essential steps to take.
Build Your Human Firewall with Security Awareness Training
Your employees are either your strongest defense or your weakest link, the choice is yours. Cybercriminals know that humans can be easier to fool than technology, which is why many ransomware attacks start with phishing scams and social engineering tactics designed to trick people into clicking malicious links or opening dangerous attachments.
Employee training transforms your staff into a “human firewall” that can spot and stop attacks before they begin. Your training should cover identifying malicious emails by looking for red flags like suspicious sender addresses, generic greetings, poor grammar, urgent language, and offers that seem too good to be true.
Teach your team to be cautious with suspicious links and unsafe attachments. When in doubt, they should verify with the supposed sender through a separate communication method. Social engineering awareness helps them recognize when attackers might impersonate colleagues, vendors, or authorities to manipulate them into revealing information or taking harmful actions.
Don’t forget USB device security, cybercriminals sometimes leave infected USB drives in public places, hoping curious people will plug them in. This training can’t be a one-time event. Cyber threats evolve constantly, so your training should too. Regular phishing simulation exercises help test your team’s vigilance and reinforce best practices without real-world consequences.
For deeper insights into these deceptive tactics and how to counter them, read our article on Avoiding Social Engineering.
Prepare an Incident Response and Communication Plan
Even with the best defenses, no system is completely immune to attack. That’s why having a well-defined incident response plan is absolutely critical. This plan needs to be created and practiced before an attack happens, so everyone knows their role and can act quickly under pressure.
If you suspect or confirm a ransomware infection, your first priority is to isolate infected devices. This means immediately shutting down affected computers and disconnecting them from the network—unplug Ethernet cables, turn off Wi-Fi, do whatever it takes to prevent the ransomware from spreading to other systems.
Once you’ve contained the immediate threat, focus on reporting to authorities. Depending on your location and the nature of the attack, this might involve local law enforcement, the FBI, CISA, or other cybersecurity agencies. Reporting helps authorities track cybercriminal activities and sometimes provides access to recovery resources like the No More Ransom Project, which offers free decryption tools for various ransomware strains.
Here’s a critical decision point: should you pay the ransom? Our strong recommendation, backed by the FBI and cybersecurity experts worldwide, is never pay the ransom. There’s no guarantee of recovery, criminals might not provide working decryption keys, or the ransomware might be “wiper malware” designed to permanently destroy data regardless of payment.
Paying also fuels future attacks by validating the criminals’ business model and often leads to continued extortion where attackers demand more money or threaten to release stolen data publicly. Instead, focus on recovery through your robust backup strategy and work with cybersecurity experts to explore available decryption tools.
Your incident response plan should be a living document that’s regularly updated and tested. When seconds count, having a clear roadmap can mean the difference between a minor disruption and a business-ending disaster.
Responding to an Attack and Securing Your Future
The ransomware landscape isn’t standing still, and frankly, neither should we. Today’s cybercriminals have turned ransomware into a sophisticated business model. They’re using Ransomware-as-a-Service (RaaS) platforms that make it easier than ever for less technical criminals to launch attacks. They’re exploiting VPN vulnerabilities to gain initial access, and they’ve moved beyond simple encryption tactics.
Modern ransomware attacks often involve double or triple extortion. First, they encrypt your data. Then they threaten to leak it publicly if you don’t pay. Some even contact your customers directly, trying to extort them too. It’s a far cry from the simple “pay us and get your files back” approach of earlier ransomware.
Your Next Steps for Comprehensive Ransomware Protection

Effective ransomware prevention requires a proactive defense mindset. We can’t just set up our security measures and forget about them. The threat landscape changes daily, which means our defenses need regular attention and updates.
Your layered security strategy should include regular security audits and vulnerability assessments. Think of these as health checkups for your digital infrastructure. Just as you wouldn’t skip your annual physical, your business systems need regular examinations to identify weaknesses before attackers do.
Continuous monitoring is another crucial element. Modern security tools can watch your network 24/7, looking for unusual activity that might signal an attack in progress.
Regular incident rehearsals are just as important as fire drills. When everyone knows their role during a security incident, response times improve dramatically. Practice makes perfect, especially when the stakes are high.
The reality is that implementing these comprehensive strategies can feel overwhelming, especially if you don’t have a dedicated cybersecurity team. Many small and medium-sized businesses find themselves caught between knowing what they should do and having the expertise to do it effectively.
That’s where professional assistance becomes invaluable. At tekRESCUE, we’ve seen how the right partnership can transform a business’s security posture. We work with companies throughout Central Texas and beyond to implement custom solutions that fit their specific needs and budgets.
We understand that every business is different. A law firm’s security needs aren’t the same as a manufacturing company’s. That’s why we take the time to understand your unique challenges, from fortifying technical infrastructure to building that crucial human firewall through employee training, and developing robust incident response plans tailored to your operations.
For expert help implementing these defensive strategies and securing your business, explore our Managed IT Services in Austin & San Marcos, Texas. We provide comprehensive cybersecurity, Strategic AI Consulting, digital marketing, and website design services to ensure your business is protected and positioned for growth.
Don’t wait for an attack to realize the importance of comprehensive ransomware protection. Contact tekRESCUE today for a consultation, and let’s build the digital resilience your business deserves.
Table of Contents









